
by Cody Jackson | Mar 29, 2019 | Aquila inSecurity
I read this morning that Taos Public Schools were hit with a widespread ransomware attack that crippled their network. I do not know how the attack was executed or spread but often these attacks are done via phishing emails or embedded malicious code in benign...
by Stephen Crim | Mar 21, 2019 | Aquila inSecurity
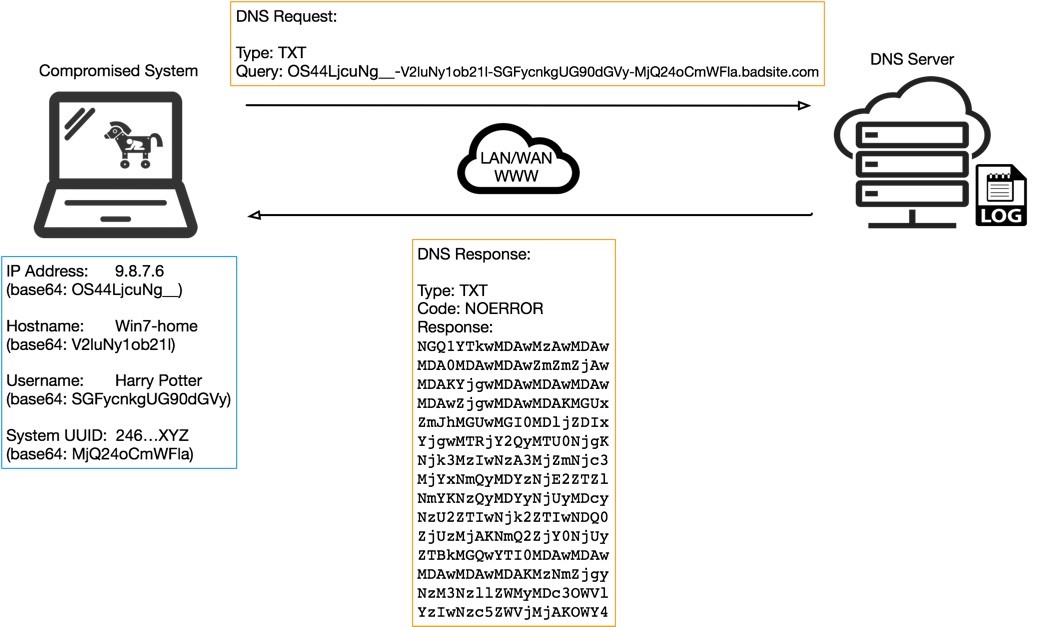
I stumbled on this excellent technical explanation of a relatively old data exfil method, using DNS tunneling. Many of us who have been enthusiasts of subverting systems going back to the 1980s have probably read ways to use exploit DNS to access the internet on...

by Stephen Crim | Mar 15, 2019 | Aquila inSecurity
When I talk about sensor-based products, what I’m specifically referring to is any product that sits outside of the traffic flow, and consumes network traffic either via a TAP/SPAN port, a packet broker or a switch with packet broker capabilities, or through...
by Damien Davies | Mar 8, 2019 | Aquila inSecurity
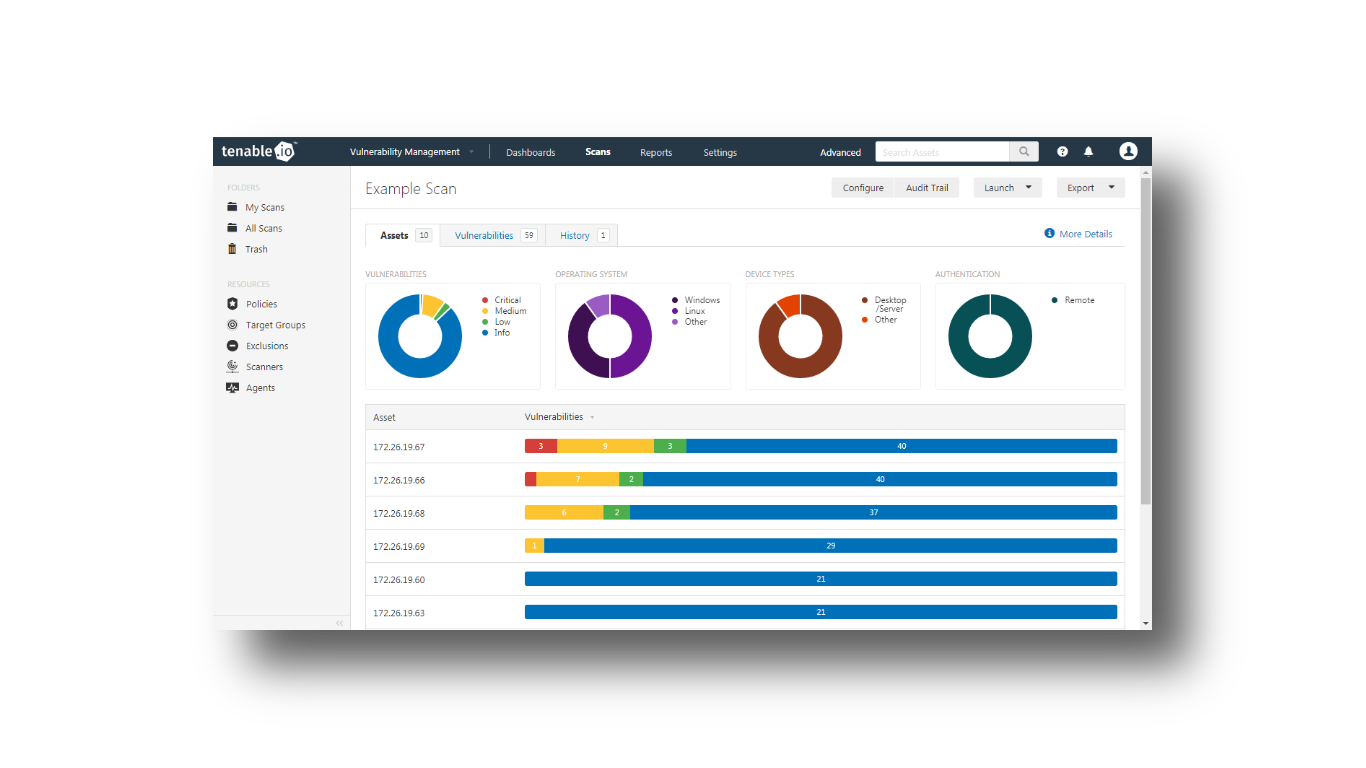
As an account manager, it is important to me that the solutions I partner with address three significant issues. The first of these is the issue of vulnerability. I am always on the hunt to find solutions that are at the cutting edge of protecting our customers’...

by Cody Jackson | Feb 27, 2019 | Aquila inSecurity
One of the key areas we can automate our defensive posture is understanding how the network we are defending looks. One of my SANS instructors once said: “you cannot protect what you don’t know about.” At the time I was working for an organization that had 12,000+...






